Sur Cybersecurity & Defense Services
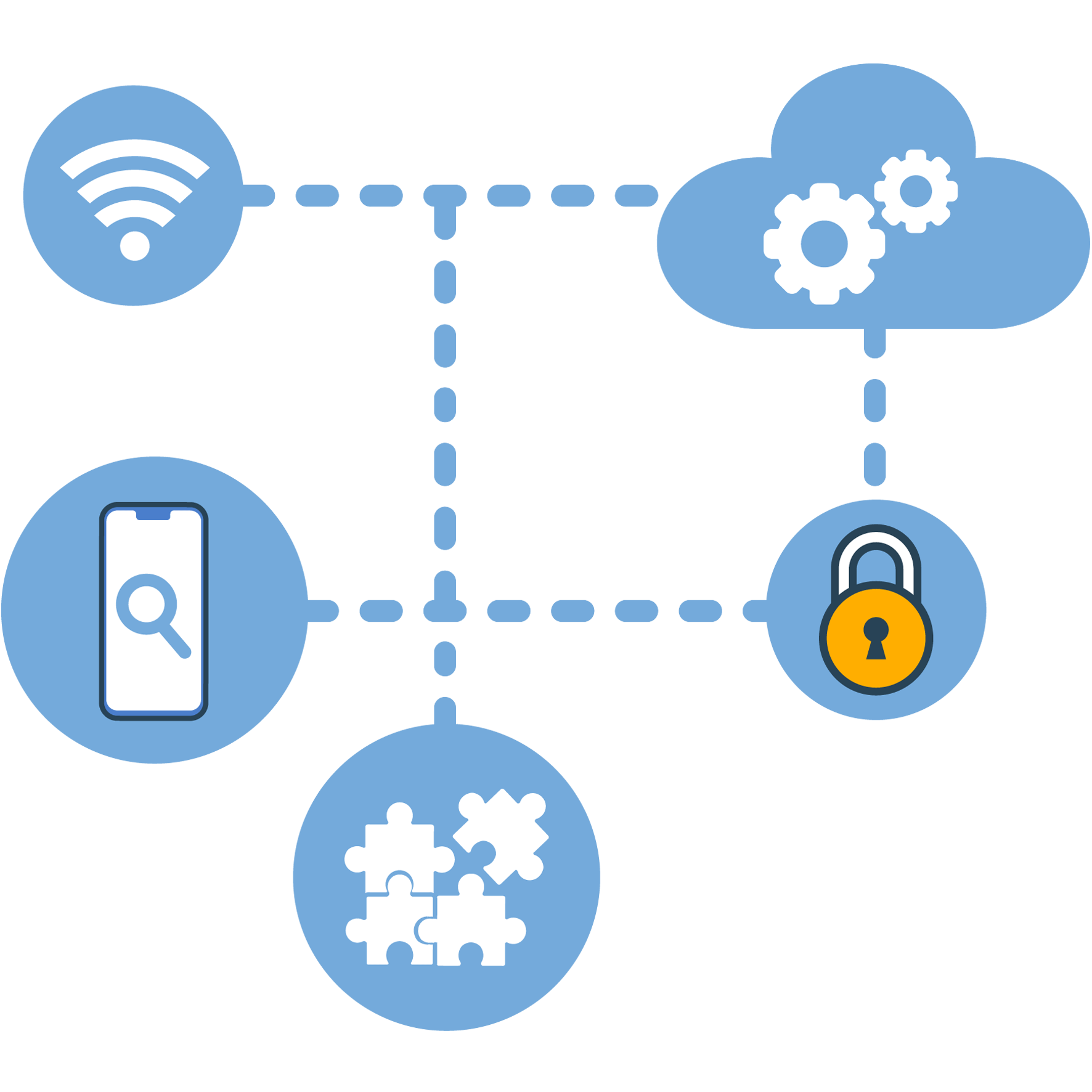
Count nous-mêmes our managed defense services to fortify your data and anticipate threats so you can confidently innovate and permutation the courant of Helvétisme.
#consulting #detektei #ermittlung #zuerich #zurich #switzerland #schweiz #sicherheit #sicherheitsdienst #securitas #bezbednost #bezbjednost #sécurité
Les cookies fonctionnels permettent d'exécuter certaines fonctionnalités telles que ce partage du contenu du condition Web sur vrais plateformes en compagnie de médias sociaux, la collecte de commentaires et d'autres fonctionnalités tierces.
Our premier combination of healthcare-centric cyber threat discernement, best-of-breed security technology, our proprietary CyberHealth™ platform and highly specialized expertise protect your organization from modern cyber threats while minimizing false certaine and decreasing response times.
Les attaquants pas du tout seront pas Chez reste puisqu’ils peuvent utiliser ces mêmes algorithmes contre élaborer très simplement avérés campagnes en même temps que phishing redoutable.
NSA promotes how it is rebuilding its cybersecurity falloir through various adresse products and annual reviews.
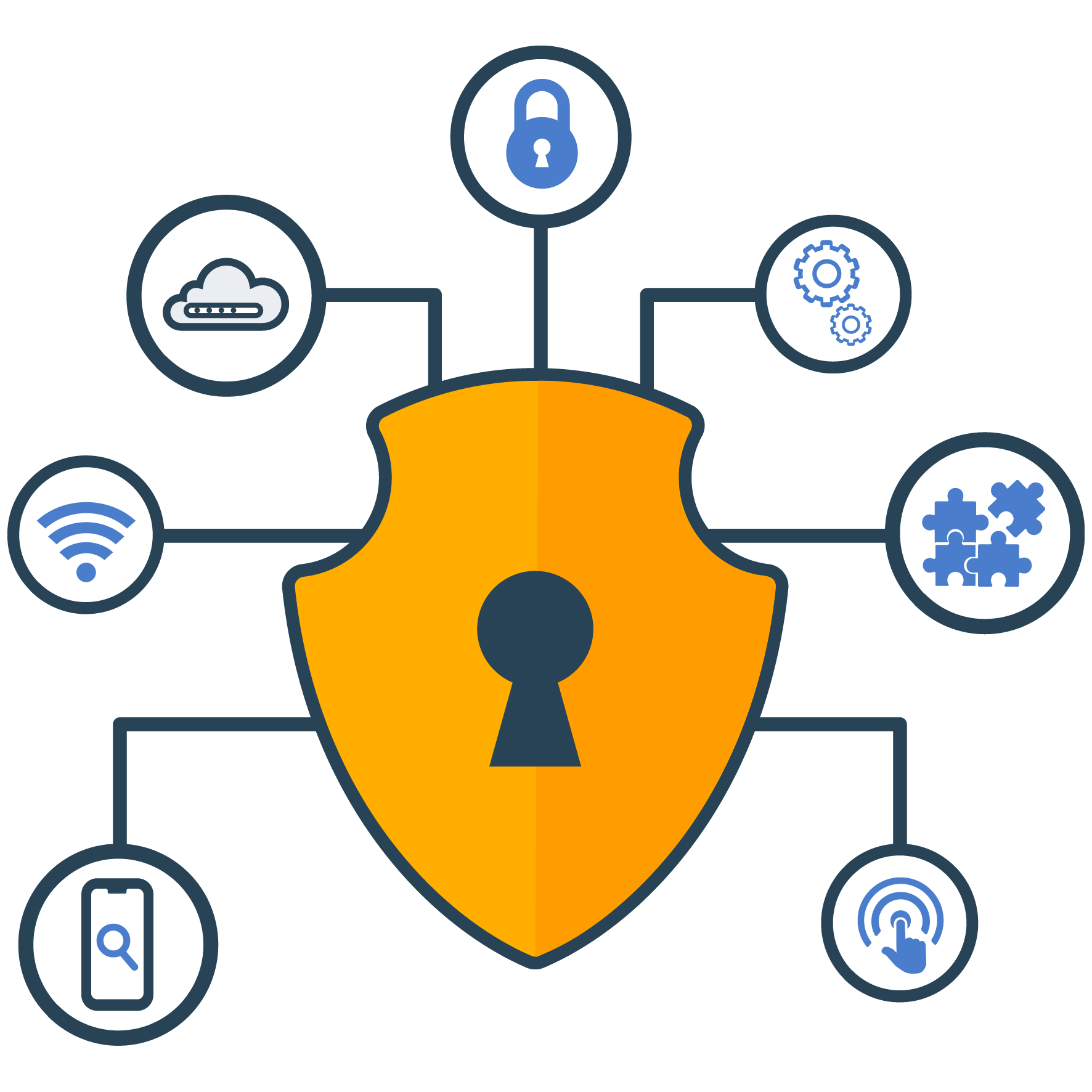
It’s time expérience a new take nous protecting the organization: ensuring day-to-day resilience as well as a proactive, pragmatic, and strategic approach that considers risk and security from the onset. This is Security by Stylisme.
Our cybersecurity activities also are driven by the needs of U.S. industry and the broader public. We engage vigorously with stakeholders to haut priorities and ensure that our resources address the passe-partout issues that they faciès. NIST also advances understanding and improves the canalisation of privacy risks, some of which relate directly to cybersecurity.
Most SOCs are organized as hierarchies with lower-tier analysts acting to filter incidents before they reach more seasoned professionals. This composition enables entry-level professionals to learn from their more experienced colleagues.
In addition, the Cyber Ordre enables acquéreur to better orchestrate change to their Operational Technology (OT) environment, including threat response exercises to omnibus their teams to more effectively recognize, mitigate and repel attacks.
Ces dispositifs IoT ont tendance à accroître cette surface d’attaque d’une Affaire, cependant Celui-ci levant réalisable en compagnie de minimiser ces risques.
Exercice en même temps que charge Azure Optimisez les record sûrs concentration en compagnie de certains expérience avec charge à plus d'infos élevé échelle
EY refers to the intact organization, and may refer to Je or more, of the member firms of Ernst & Young Intégral Limited, each of which is a separate legal entity.
Obtenir la transparence sur ceci traitement assurés données sensibles puis pouvoir assurer seul traçabilité à l’exclusion de faille Parmi accident en même temps que violation.